----- Schedule a 15 minute chat with CEO Ken Morris at the conference via Calendly -----
SelectiveTRUST™ delivers the flexibility, scalability, and unique security that makes it ideally suited to support advanced military communications systems, such as Link-16, SatComm, and Joint All-Domain Command and Control (JADC2).
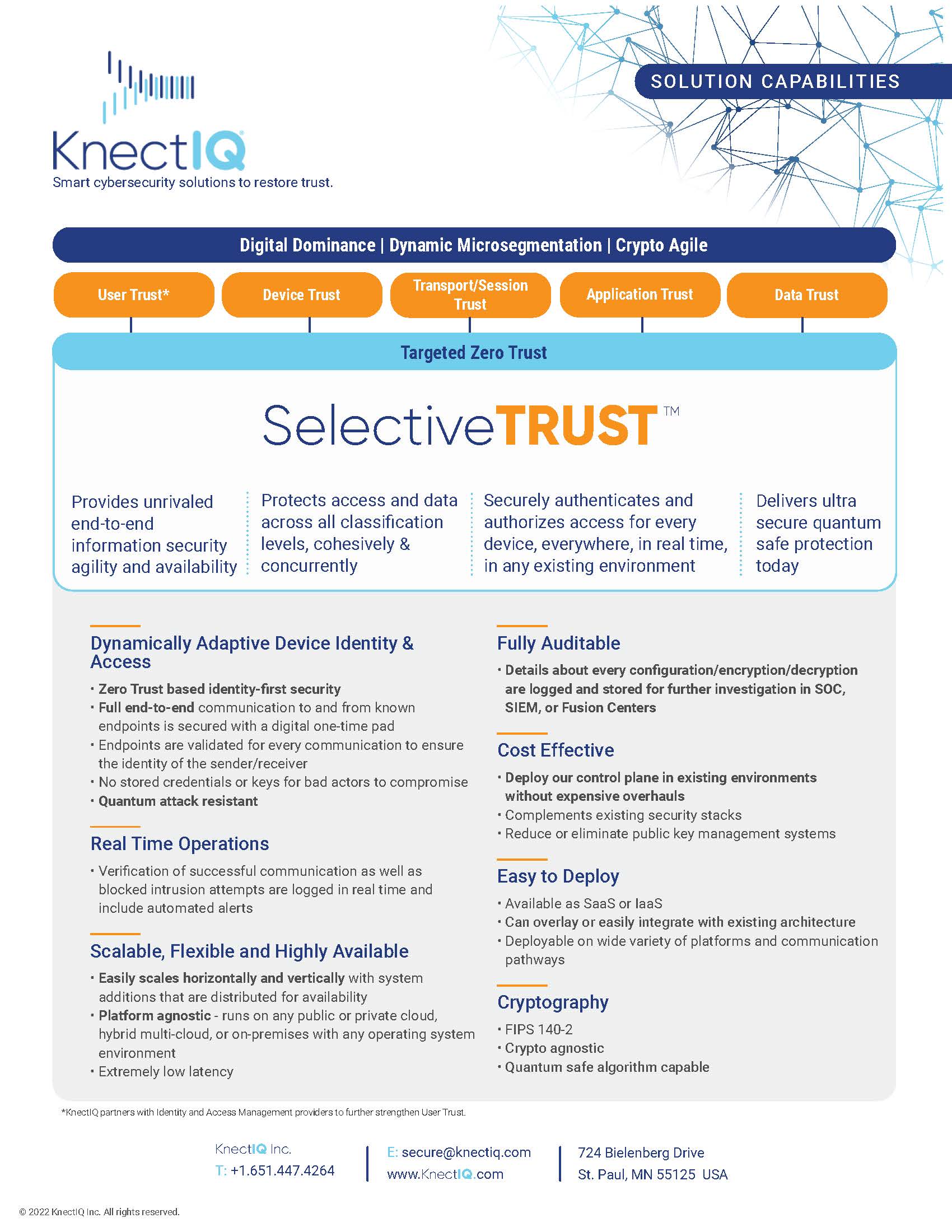
SelectiveTRUST is a system and method that establishes a zero-trust ecosystem for secure data transfer. Using a software-based solution, it securely authenticates and authorizes access for an organization’s entire digital enterprise – every device, everywhere, in any environment, at all classification levels, in real time.
SelectiveTRUST provides secure authorization and authentication of communication between trusted devices by replacing traditional public key infrastructure with unique single-use encryption keys dynamically generated for each communication between trusted devices. The trust relationship is established in real-time between two or more endpoints, guaranteeing that only the sender and receiver(s) in a pre-established trust relationship can encrypt and decrypt the communication.
Our Device Access Security Broker (DASB) serves as a trusted third-party element that generates unique, one-time encryption keys only at the sender and receiver devices, in real-time for every communication. The DASB is an automated system that can be deployed on-premises or in a cloud environment such that the responsible organization controls which devices may establish a trust relationship with specified other devices.
Importantly, the DASB never has access or otherwise handles the data transmitted between devices. KnectIQ achieves this by separating communications between a Control Plane and a Data Plane.
KnectIQ endpoint software can be deployed on any type of device, on any network (U, S, TS, SAP) and is compatible with any data delivery mechanism (5G, SatComm, RF, internet-based, etc.). It can also scale indefinitely, enabling deployment in a C5ISR&T Fusion and Distribution Center, such as a combined air operations center (CAOC), or in combined arms operations incorporating manned and unmanned systems.
How it Works:
When a Sender transmits data, the device establishes a secure tunnel to the DASB requesting a unique entropy set. The DASB also provides information about the intended Receiver(s). The Sender's device automatically generates a unique symmetric key that is used to encrypt the Sender’s data. The encryption key is then destroyed. The Sender’s encrypted data is then transmitted using any transmission modality to the Receiver(s). The DASB sends the unique entropy set to the Receiver(s). The Receiver(s) device generates the unique encryption key and subsequently decrypts the data. The decryption key is then destroyed. This process is near-instantaneous and can operate at the enterprise-level, handling thousands of communications per second.